When running the Qualys scanner on the Artica you should see this threat:
QID: 62046 CVSS Base: 5
THREAT:
Successful TCP connections were established to open ports on the host using the CONNECT method allowed by the HTTP proxy server.
IMPACT:
This vulnerability may be exploited to connect to your internal network that is otherwise unaccessible.
SOLUTION:
Reconfigure your proxy server to disable the CONNECT method or restrict its access.
This security hole is a default configuration that allows the proxy to relay all ports to the destination.
If your proxy allows access to untrusted hosts or users, you can be sure that people will find and abuse your service.
Some people will use your proxy to make their browsing semi-anonymous.
Others will intentionally use your proxy for transactions that may be illegal (such as credit card fraud).
A number of web sites exist simply to provide the world with a list of open-access HTTP proxies.
You don’t want to end up on this list.
To avoid this issue, you need to reduce the allowed forward destination ports.
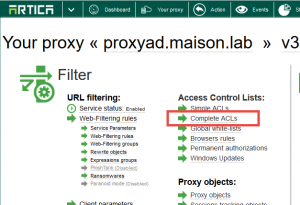
- On your proxy section, choose “Complete ACLs“
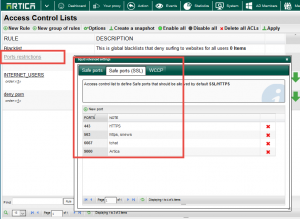
- On the table, click on the Ports restrictions gray link.
- Add/remove all allowed ports in both HTTP/HTTPS protocols.
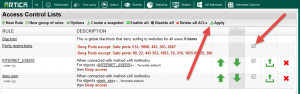
- Turn on the rule by click on the checkbox in the row.
- Click on Apply button to make rules in production mode.